Code for an Enigma simulation is incorporated into a program of two parts The first part is simply an Enigma that allows the encryption of a text Starting states may be chosen freely Five wheels are available, and a Steckerboard may be used The second part needs as input an encoded text and a number of characters known to be the plain text, ie a crib The program then iteratesThe Enigma code was first broken by the Poles, under the leadership of mathematician Marian Rejewski, in the early 1930sIn 1939, with the growing likelihood of a German invasion, the Poles turned their information over to the British, who set up a secret codebreaking group known as Ultra, under mathematician Alan M TuringBecause the Germans shared their encryption device What Made the Enigma Code Special?
The Enigma Machine And The Ultra Secret South African Military History Society
Enigma code example
Enigma code example- PyEnigma is a Python 3 library for simulating the Enigma machines used by the German armed forces (Wehrmacht) during World War 2 PyEnigma makes it possible to both encrypt and decrypt messages that can be sent to, or received from, actual Enigma machines used by the German army (Heer), air force (Luftwaffe), and navy (Kriegsmarine) It is my hope that library will be useful to Enigma Hunting for clues Soldiers would search enemy command posts for code booksRadio operators would record scrambled messages and analyze their patternsSailors would scramble to search captured or wrecked ships for surviving code sheetsSpies sought out technical information or other ways to undermine the Enigma project The information they gleaned from different



The Enigma 1
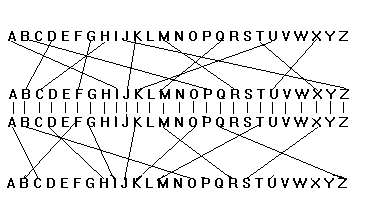
For example, in Big Brother the The crime drama 'Shetland' uses enigma codes to slowly reveal the narrative as DI Perez unravels the case Action codes These are actions in the narrative The ENIGMA code is symmetric the same settings are used for encryption and decryption These settings are the enciphering "key", and they cannot be sent to the receiver over an insecure communications line (radio, telephone, and so on) The other entries in the ENIGMA manual have to do with groups of three letters (Renngruppen) encoding the settings of theFor example, suppose we wanted to encrypt the message bed with the following simplified Enigma machine that is limited to a six letter alphabet Figure 4 Simplified version of a Enigma machine with one rotor The disk on the left is the keyboard, the middle ring is the rotor, and the disk on the right is the lampboard The wiring of the rotor
An example of the basic Enigma Tony Sale's Codes and Ciphers This is a supplementary page illustrating Tony Sale's sequence of pages on the Enigma A detailed working through of Enigma encipherment The Enigma machine gives a mechanised way of performing one alphabetic substitution cipher after another In this example we are only concerned with the enciphermentIt's packed full of information about all sorts of codes, including the famous story Enigma, the code machine used by the Germans during WWII The Germans thought their code was invincible, but incredibly, British mathematicians managed to break the code and read all the messages sent by the Germans during the war Historians think that having this inside information shortened theThe Enigma code is set in a crossword format, each row or column will spell a word when completed correctly;
In terms of Music Video • Barthes' Enigma Hermeneutic Code can be found in a majority of music videos • The narrative will establish enigmas (puzzling imagery or occurrences) or mysteries as it goes along • Essentially the narrative functions to first establish then solve 9 Example of Enigma Code • Katy Perry – Wide Awake 10 So how about using the Enigma Code Machine to generate secure passwords for us Dr Frank Spiess helps us out here with a very good flash Enigma Code Machine A brief example Open the machine window, click on the "Input" textbox and enter "c" on the keyboard The plugboard leaves C as C while highlighting the specific wire in red The electrical current thenEnigma decoder Decrypt and translate enigma online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today ZBase32 Hex to Base64




Cryptanalysis Of The Enigma Wikipedia



What Alan Turing Can Teach Us About Product Management Chargebee S Saas Dispatch
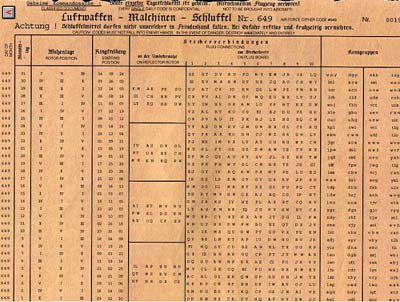
This code, along with enigma codes can create considerable suspense Think about how many How Allied forces cracked Enigma code Enigma code used by German forces during World War II Thought to be unbreakable Britain cracked the code and saved millions of livesMilitary Use of the Enigma Tony Sale's Codes and Ciphers This is Page 3 of Tony Sale's sequence of pages on the Enigma, explaining how the Enigma was used in German military practice, and outlining the problem facing anyone trying to break the system The Message Key and Setting Sheets As mentioned on page 1 of this sequence, the message key, (the complete and exact




Enigma Machine How Does The Famous Encryption Device Work Dev Community



Enigma Paper Enigma Franklin Heath Ltd Wiki
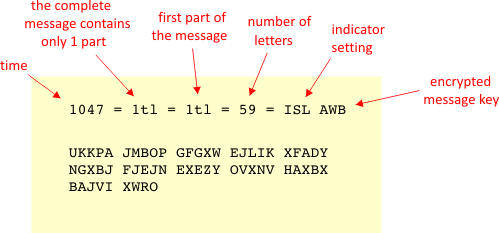
Enigma codes entice the audience to watch the rest of the film as they're curious as to what will happen next;As characters in social realism films are involved in crime or anti/social behaviour,the audience is often left to decide whether or not a character is a protagonist or an antagonist, until this is blatantlyThe number "65" represents the number of letters in the actual message, so the Radio Operator and Enigma Decoder can confirm they have the entire message The "=" are just place holders, much like a STOP in a Telegram or, in the case of Enigma, an "X" You'll find these throughout the body of the message FEW GHT =




Ukw D
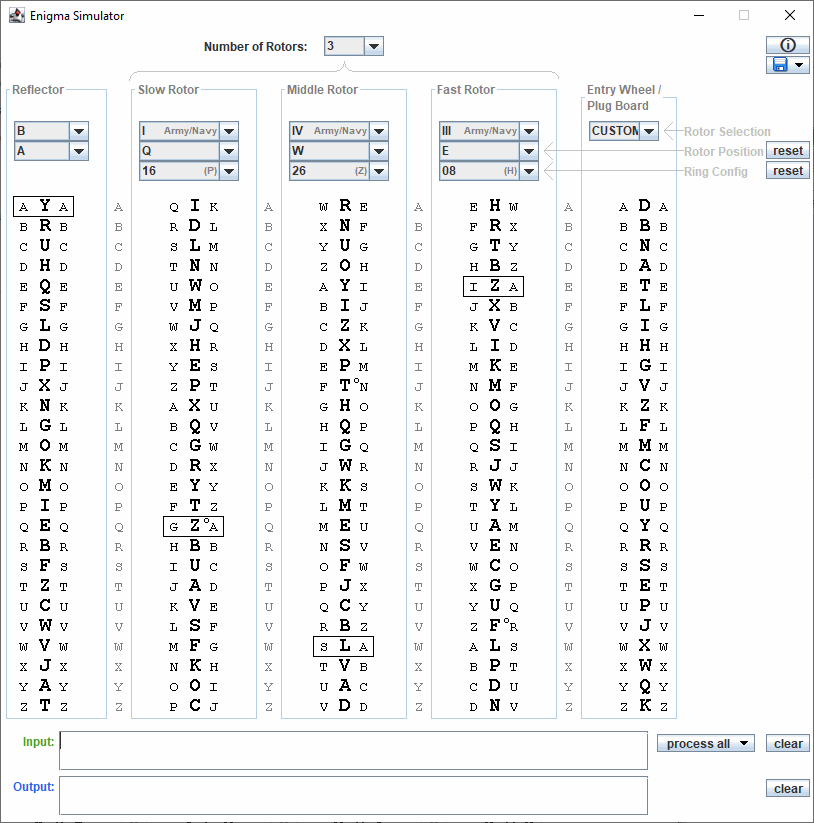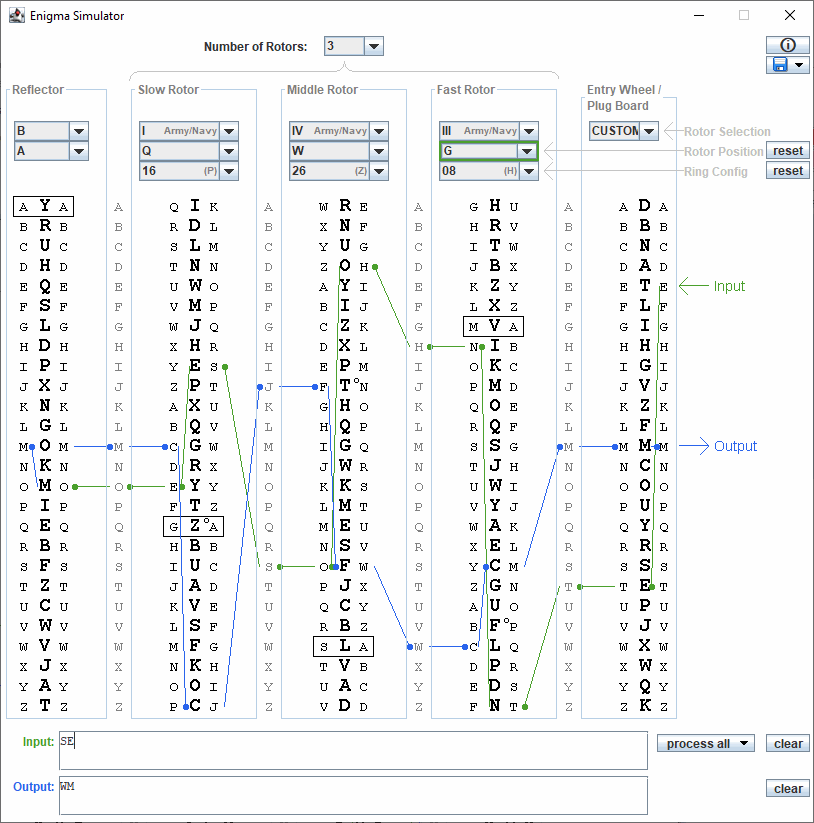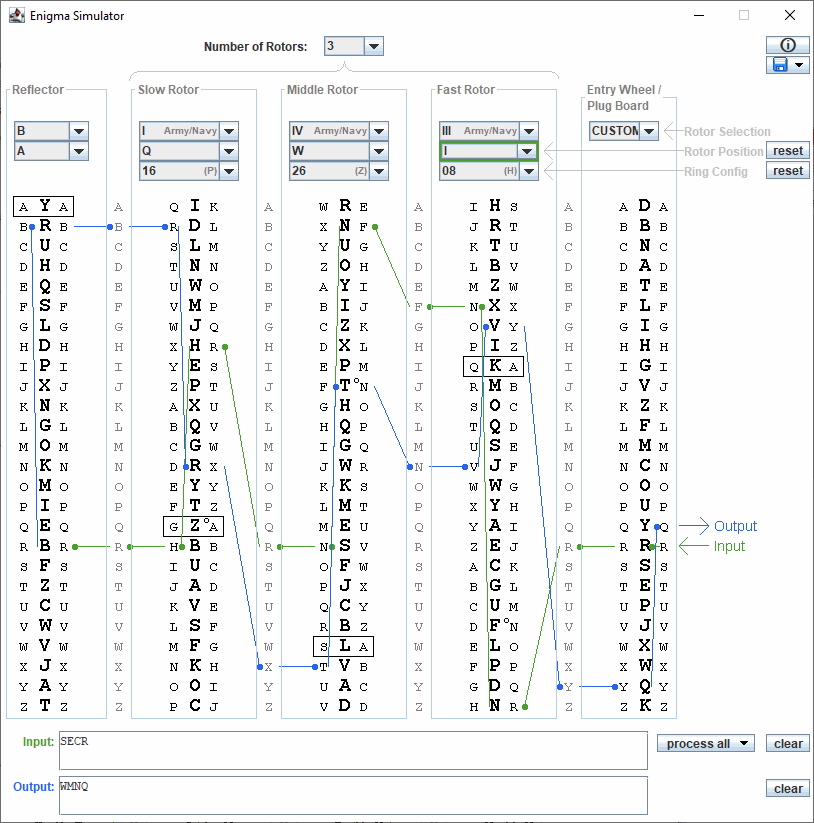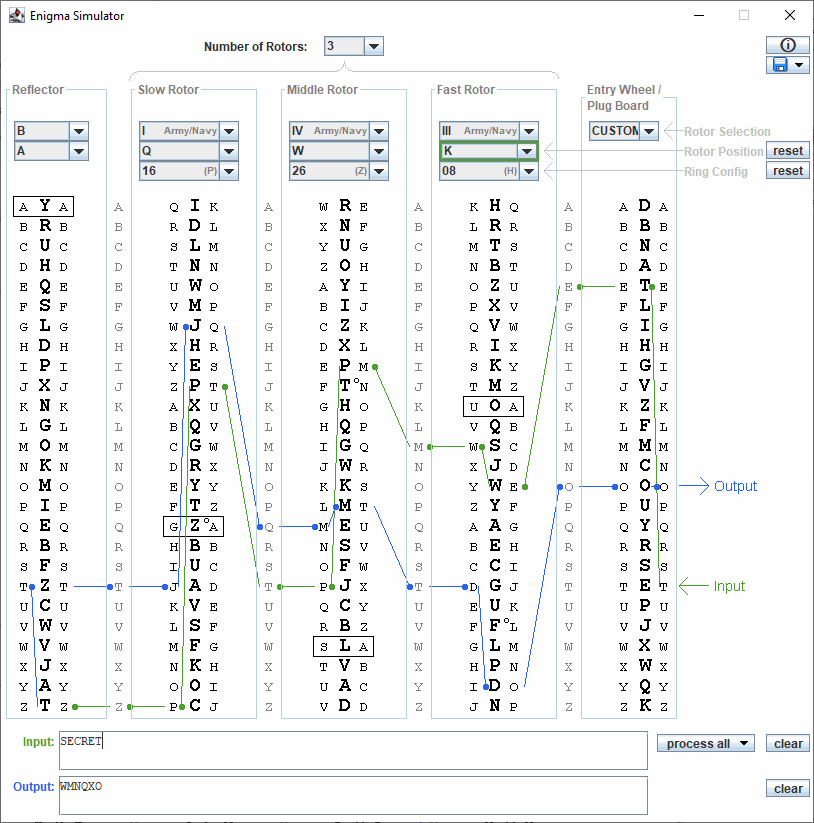



Enigma Simulator
The main focus of Turing's work at Bletchley was in cracking the 'Enigma' code The Enigma was a type of enciphering machine used by the German armed forces to send messages securely Although Polish mathematicians had worked out how to read Enigma messages and had shared this information with the British, the Germans increased its security at the outbreak of war by An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakable Alan Turing and other researchers exploited a fewAlternatively, if you'd like to play offline simply, select the print button to print the puzzle and complete in written format All GAME FUNCTIONS Use your understanding of the English



The Enigma Machine And The Ultra Secret South African Military History Society
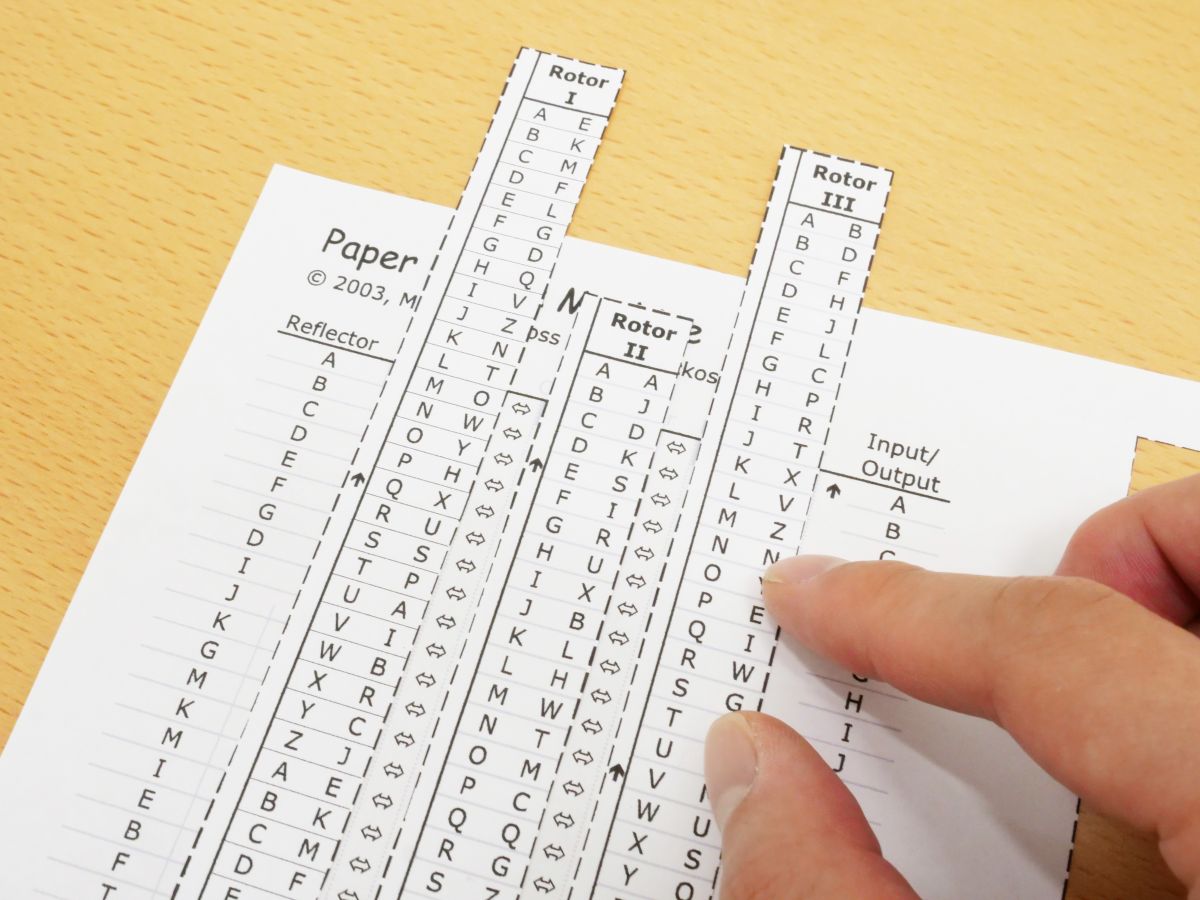



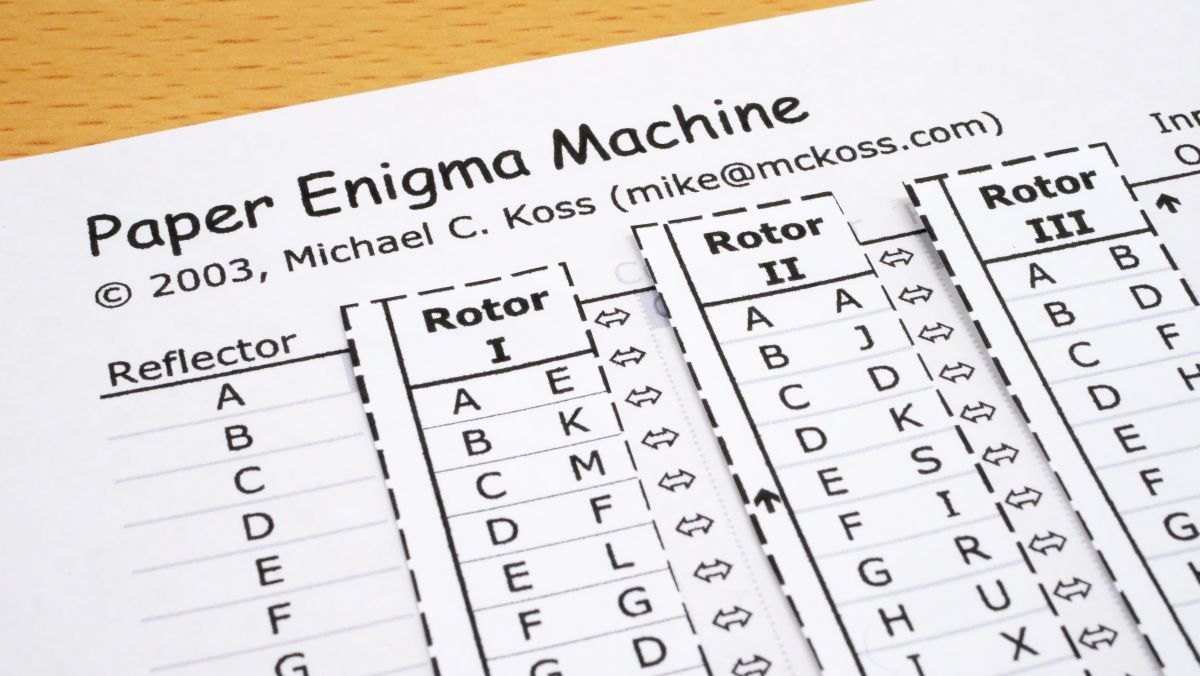
I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine
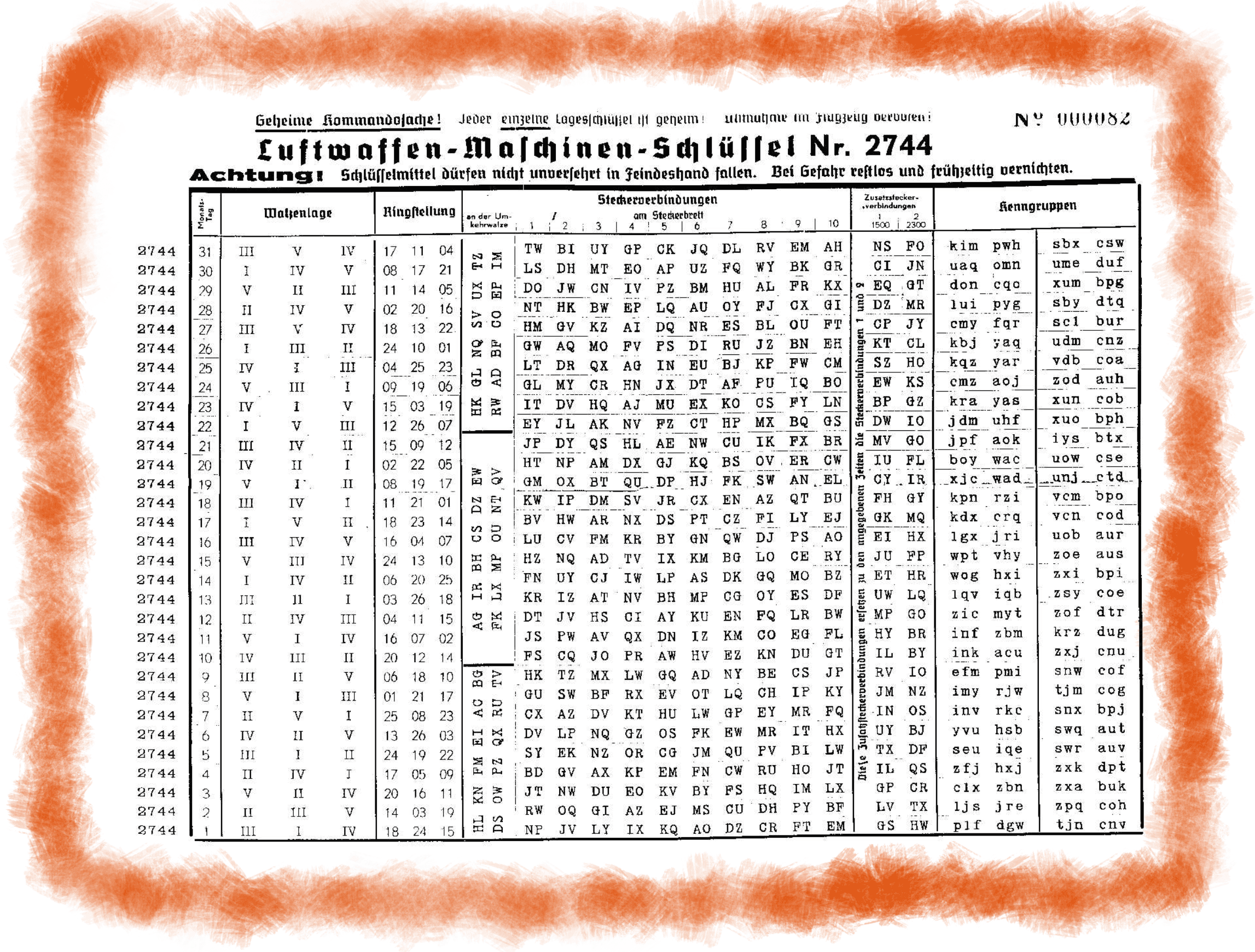
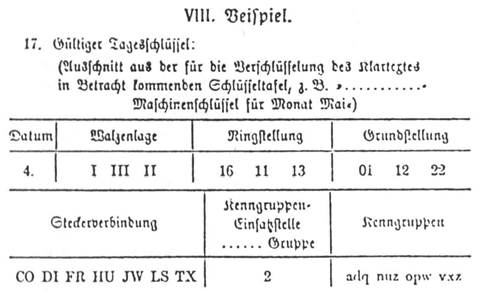
Begin by typing code from the directory that contains the starter code enigmaml That will open your project directory in VS Code of the rotor Here, for example, is a closeup of a threerotor Enigma machine in which the top letters are currently RDK When a rotor is in its default orientation, with 'A' showing as the top letter, the offset of the rotor is 0 current entering at3 How the Enigma was Set Up and Operated The operator was provided with a code book which he consulted at midnight which was when the new key for that day came into effect The code book listed the five parameters for setting up the Enigma 1 The Datum or date 2 The Walzenlage or rotor order for that date For example IV, I, V 3The Enigma machine Encrypt and decrypt online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Caesar cipher Bitwise calculator Binary decoder



Enigma Slide Rule Cipher Linear Cipher W Numbers Characters



2
Operation of the Enigma machine with an example Basic handling After preparing the setup for the machine (wheel numbers, wheel order, ground setting, ring setting, plug) scrambling messages is very simple You press a letter of your plain text and a lamp indicates the enciphered letter You write down this scrambled letter and press the next one The Enigma machine is symmetrical,The international QCodes are a good example of this During WWII, codebooks were often used to encrypt a message, sometimes in addition to other cryptographic methods, such as Enigma or hand ciphers Cracking a codebook is a difficult but not impossible task for a codebreaker Once a codebook is captured or reconstructed, messages are noThey also help to move on the narrative Action Codes Action codes are significant events which move the narrative on in a particular direction For example, a phone ringing or a knock at the door Both actions are used to change the
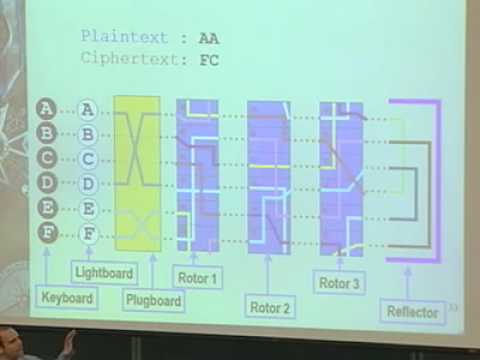



The Enigma Code Youtube




Barthes Enigma Code
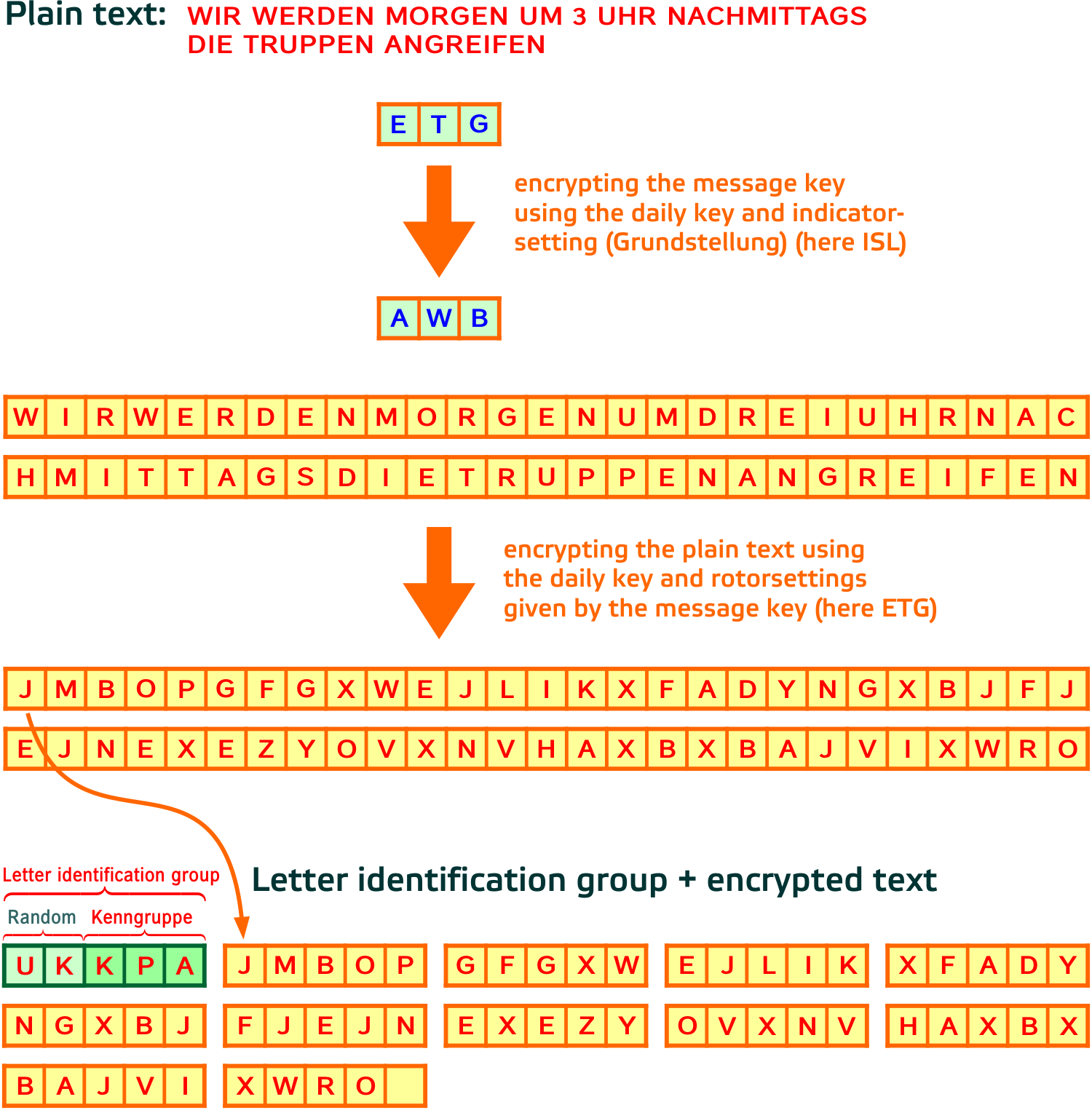
The Enigma Code was generated using a device called the Enigma Machine The machine consisted of a series of rotors, a keyboard to type the code, and a plugboard which operated much like an oldfashioned telephone board The machine was set at the start of each day, with three rotors selected and the plugboard arranged Using this method of encryption, it was possible to program the Enigma But dr(R * (T1)) is the code segment from the previous tumbler For the first code segement we get the very simple solution R In words The code segment of the first tumbler is R To caluculate the next code segment take the code segment for the previous tumbler, add R to it If the result is larger than 9 add the first digit of the result toBreaking the Enigma Codes For my example I will shorten the crib slightly to develop a Bletchley menu Note that this menu has two loops D V S A J I E D S A X V Also note relative positions of the rotors as the cipher text proceeds Using the smaller loop, we shall see that we have enough information to begin our break of Enigma code Courtesy of the Rutherford Journal Centre for




How Did The Enigma Machine Work Computing The Guardian



The Human Errors That Defeated Enigma Openmind
The Enigma Code is a cipher generated by something called the Enigma Machine The Enigma Machine played a crucial part in communication among the Nazi forces during World War II It was used to encrypt highly classified messages, which were then transmitted over thousands of miles to the Nazi forces at the front using Morse codeOne would wonder why the encryption mattered anyway, and why it took a lot of effort to decode it The quality of codes is determined by the number of possibilities of getting the correct answer In the case of the Enigma code, one had to get all settings on the Enigma machine right before you could decode itAction and Enigma codes – Roland Barthes 1 Willow Catlin 2 Roland Barthes was a literary theorist that studied structure and semiotics in literature Action and Enigma codes are one of the 5 codes Barthes designated to understanding structuralism of narrative The other three codes are the semic / connotative code, the reference / cultural code and the symbolic code 3 The Action code



Enigma Procedure




Octapi Brute Force Enigma What Is Enigma And How Does It Work Raspberry Pi Projects
We have given you a starting either a letter or letters to get you started!Enigma Codes are collectible items found in Wolfenstein The New Order and Wolfenstein II The New Colossus The collectible Enigma Code fragments are hidden in the game world, appearing as red booklets with a black Wolfenstein logo on the cover, followed by the words "GEHEIM Enigma Codes" Most code fragments are scattered about in the open just up for grabs, though othersFor example, Enigma machines were not carried by ships that might be captured or run aground of wolfpack attacks following the strengthening of the encryption might have given the Germans a clue that the previous Enigma codes had been broken However, that recognition did not happen because other things changed at the same time, the United States had entered the war and




11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium
Some examples of popular enigma codes in social realism films are The audience is often left to wonder why characters behave in a certain wayCan certain characters be trusted?Translation of "EnigmaCode" in English Enigma Enigma Code code coding passcode cipher coded Other translations Wenn Sie nach diesem Tutorial werden Sie nun in der Lage zu verstehen, und EnigmaCode Api If you followed this tutorial you are now able to understand code and Enigma Enigma codes allow the audience to question certain aspects of a film Within film, the use of the enigma is much more common in the horror and drama genres These are films that rely strongly on suspense to generate the right effect on the audience, and enigma codes help to enhance thisThe film Law Abiding Citizen is from a mixture of suspensereliant genres such as



Pdf The Cryptanalysis Of The Enigma Cipher The Plugboard And The Cryptologic Bomb



The Enigma Machine And The Ultra Secret South African Military History Society
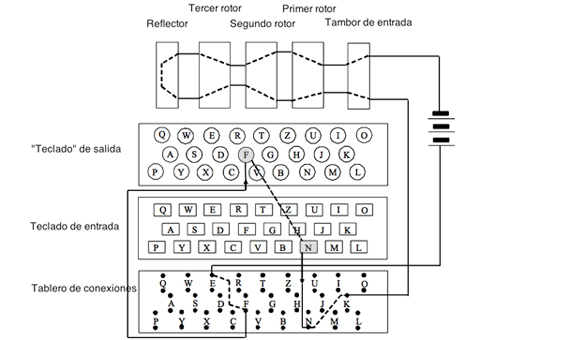
The Enigma machine resembles a typewriter and has several codewheels that can be rearranged and adjusted to vary the coding algorithm The example shown has three code wheels, a "reflector" wheel, and a plugboard, all of which were set up each day according to a codebook that every operating unit had The message was then typed into the keyboard and aHow to use the Paper Enigma MachineHere's a link https//wwwapprendreenlignenet/crypto/bibliotheque/PDF/paperEnigmapdfSpecial thanks to Michael Koss Proairetic/ action code Parts of a narrative which are related to things happening For example "Gus glared at Gary, and started to crack his knuckles threateningly" At this point, the audience would probably guess that Gary is going to get punched!



Description Of The Enigma




The Enigma 1
This example, taken from the W Book, forms into four groups of four letters Then the code breakers could reconstruct the Weather Short Code letters the Enigma operator had keyed in They had a crib zabcdefghij KQJ MUAU JSEL cipher ZYR QSOV KVQM crib So now work out a Menu for the Bombe to break the original Enigma settings The first thing to spot is a loop S dLinguist Roland Barthes described Five Codes which are woven into any narrative The Hermeneutic Code (HER) The Hermeneutic Code refers to any element of the story that is not fully explained and hence becomes a mystery to the reader The full truth is often avoided, for example in Snares deliberately avoiding the truthBreaking the Enigma Code In the early days before World War II, both the Polish and British codebreakers had examples of Scherbius ' commercial machines, but not the German military's rotor wheels The Poles realised that it was necessary to use mathematics to look for patterns to break modern codes and had broken some of the early prewar German codes while the British



Exploring The Enigma Plus Maths Org



2
I would really appreciate some help Note I used the 1998 version of C instead of C 11 or C 14 because I needed access to the auto keyword to store the raw data of a function instead of the output //Enigma Machine #include #include #include #include #include #include #include
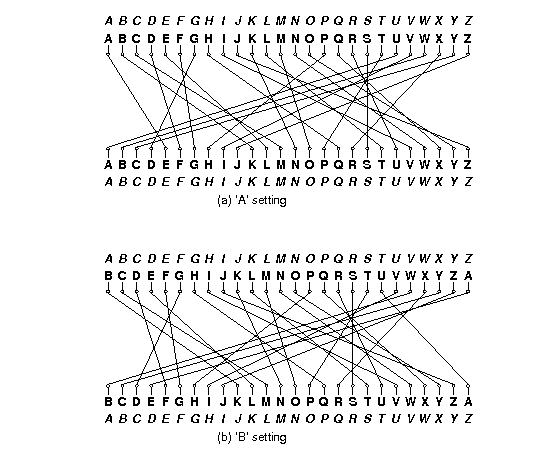



Project 1 Cs 61b Spring




Enigma Machine S Hebrew Secret The Times Of Israel




Enigma Machine Used By Nazis To Send Coded Messages During Ww2 Set To Go Under Hammer Mirror Online
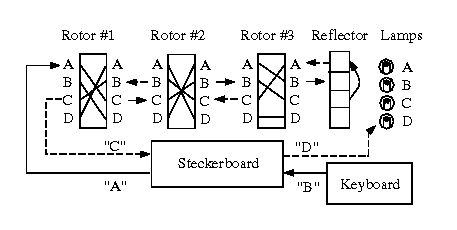



Cryptology I Vigenere Based Systems




Breaking Enigma A Story Of European Co Operation Science Museum Blog



Enigma Procedure



The Polish Attack On Enimga




How Many Enigma Machines Are There Left Dr Enigma




Operation Turing What Is Kenngruppen




How The Enigma Works Nova Pbs




M4
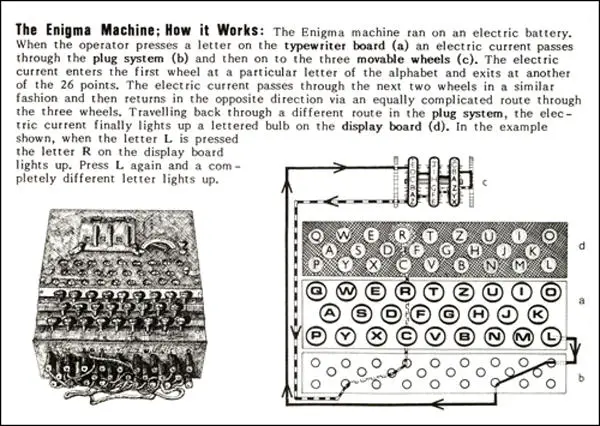



Enigma Machine



3



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




Cracking Enigma




Roland Barthes Codes Theory Roland Barthes Basic Info
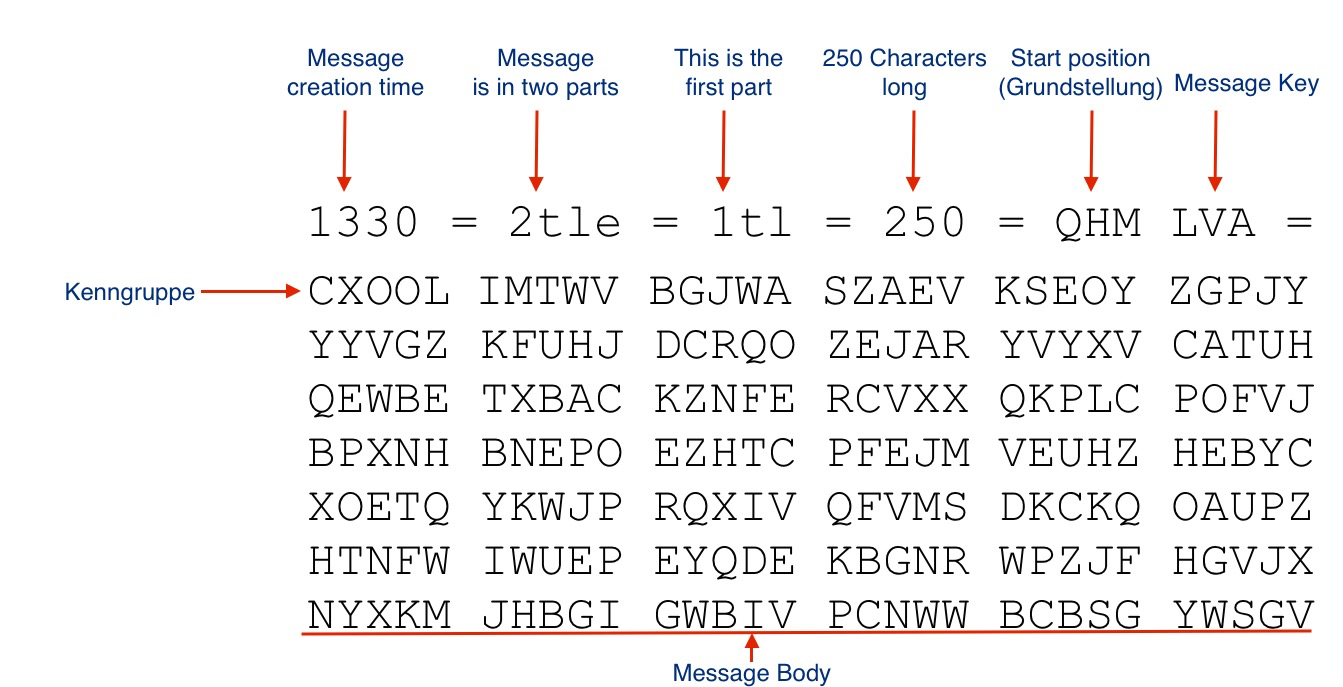



Enigma Historical Lessons In Cryptography Jgandrews Com




Enigma Cryptography World War And Alan Turing Commonlounge



2



A1 Enigma Cs 3110 Spring




Enigma Slide Rule Iinear Cipher Encryption Machine Youtube



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




Enigma Roi Extraction Protocol Enigma Ucla




How To Crack The Enigma Code Calculate




Lecture On Naval Enigma Tony Sale




Enigma Codeproject



1



Enigma




The Enigma 1



1




Building An Enigma Emulator And A Bombe



2
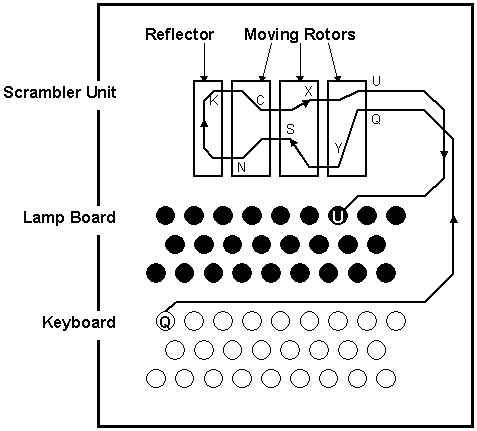



Enigma And A Way To Its Decryption
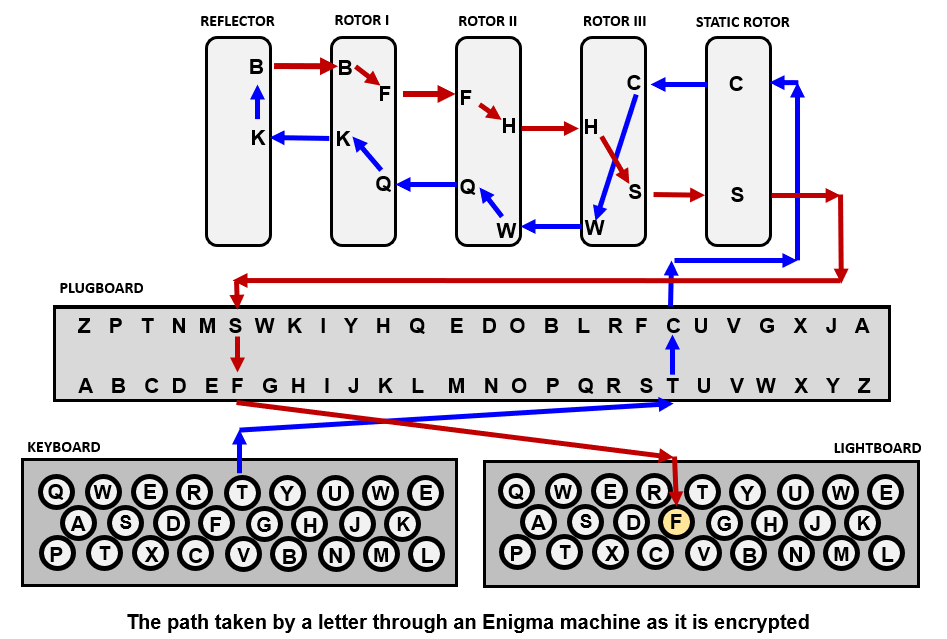



Modern Era University Of New England Une



Alan Turing Machine Computer Scientist Great People



1




Enigma Machine Brilliant Math Science Wiki




The Enigma Enigma How The Enigma Machine Worked Laptrinhx




Codebreaking Has Moved On Since Turing S Day With Dangerous Implications
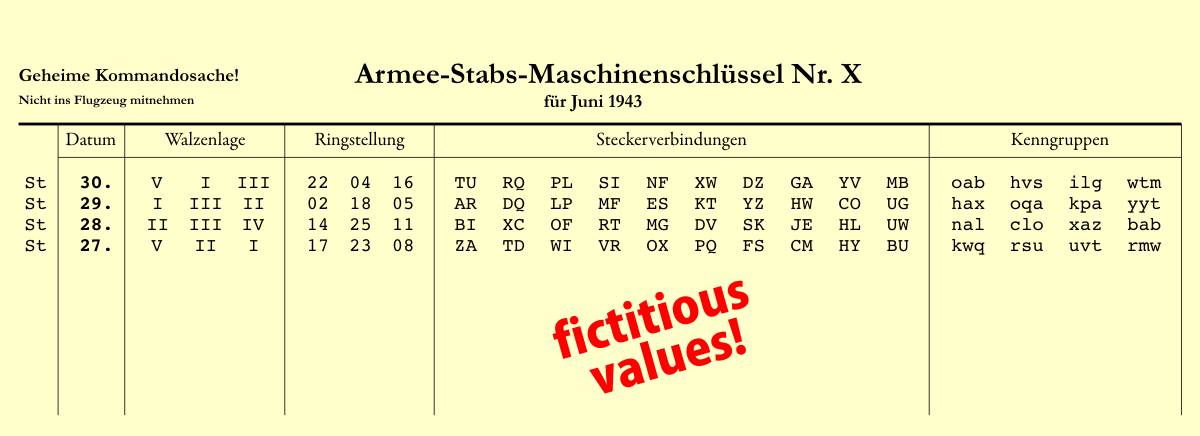



Enigma The German Cipher Machine




Charlesreid1




Enigma Daily Settings Generator 101 Computing




Ic211 Oop And Enigma



Enigma Cipher



Enigma Background



Operation Of The Enigma Machine With An Example




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium



What Is The Modern Equivalent Of Wwii S Enigma Machine Quora



2




The Enigma Cipher Machine And Breaking The Enigma Code
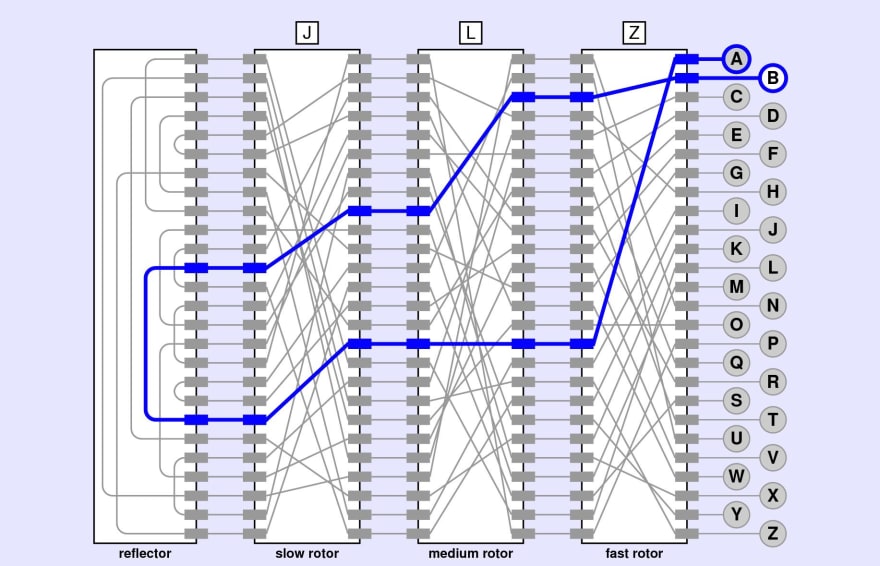



Enigma Machine How Does The Famous Encryption Device Work Dev Community



Gc1vz Darwin Enigma Challenge Unknown Cache In Northern Territory Australia Created By Gibbo003



Exploring The Enigma Plus Maths Org



Enigma Encoder 101 Computing



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




7 Sendng Your Message Enigma




Enigma Machine Wikipedia




Pdf The Cryptanalysis Of The Enigma Cipher The Plugboard And The Cryptologic Bomb




You Can Copy And Paste Number Six Right Here From Chegg Com



Enigma A Pictured Step By Step Howto About Encryption



Enigma The German Cipher Machine




The Human Errors That Defeated Enigma Openmind



2



Enigma Codeproject




The Norrkoping Enigma Messages How To Break The Air Force Enigma Machine
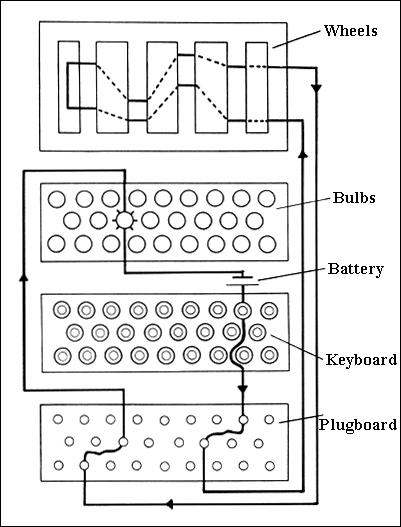



Enigma Machine




Enigma Technology And The History Of Computers



Understanding The Enigma Swimming The Styx




The Enigma Cipher Machine And Breaking The Enigma Code




Cryptanalysis Britannica




Project 1 Enigma
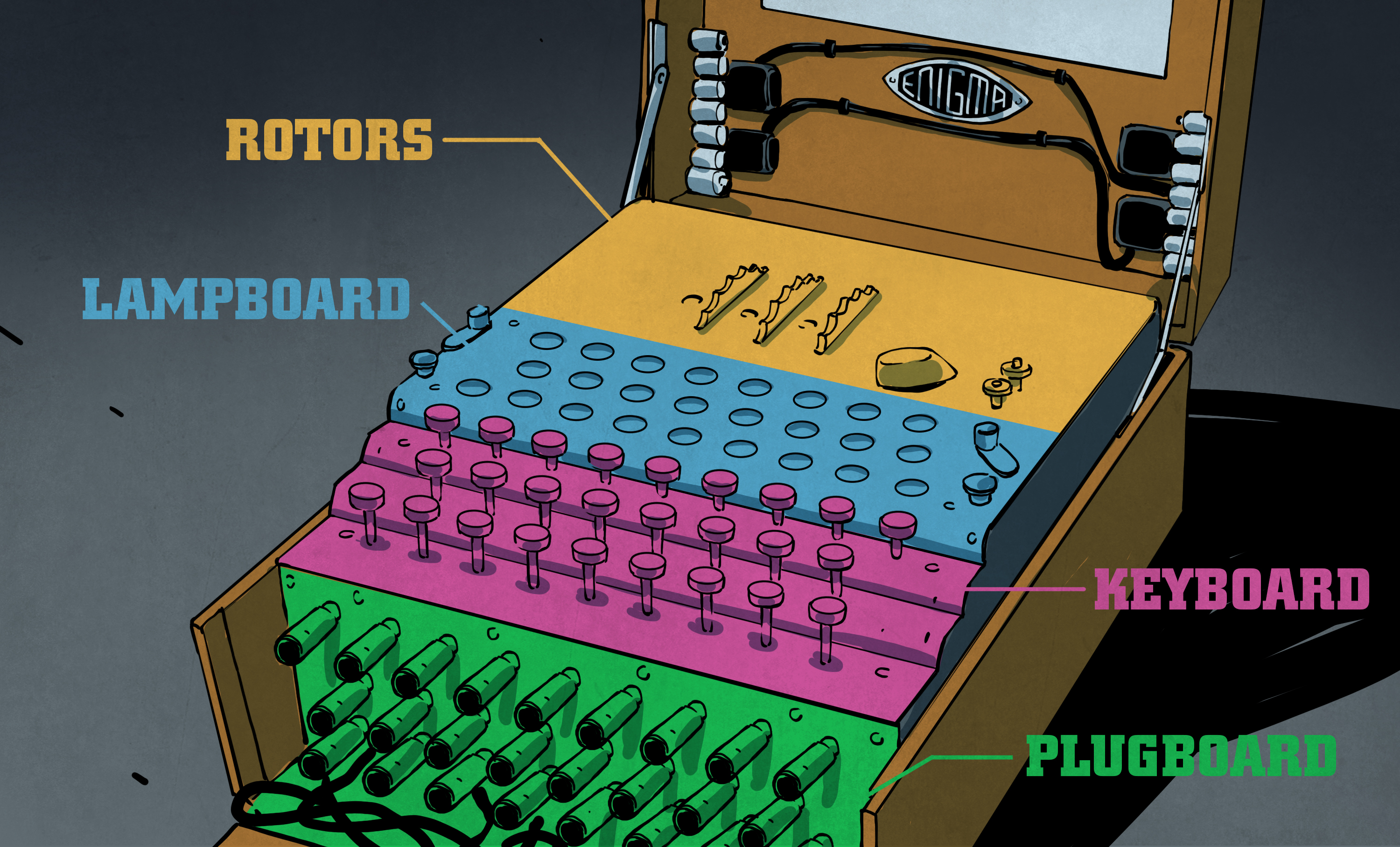



The Enigma Enigma How The Enigma Machine Worked Hackaday




11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond



Enigma C
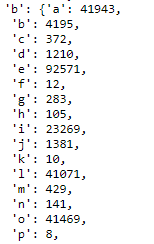



Breaking The Enigma Code In Python With Mcmc Marvel Themed By Jack J Towards Data Science



Enigma The German Cipher Machine




Enigma Codes Wolfenstein The New Order Wiki Guide Ign




Hacking Homeschooling Codebreakers And Ww2 Histories Of The Unexpected




Enigma Code Broken World War Ii Database



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



0 件のコメント:
コメントを投稿